At some point (pre-2012), I signed up for G-Suite that had a limited but free set of services. I’ve continued to use those services, but wondered if I could federate this into my AWS environment. Seemed simple enough. You will need admin permissions both in your AWS account as well as G-Suite.
G-Suite Steps
Log into your G-Suite Admin console https://admin.google.com and select “SAML Apps”
Amazon Web Services is a preconfigured application to add
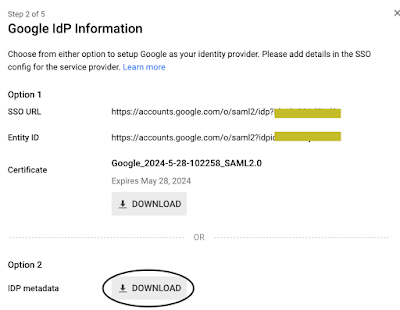
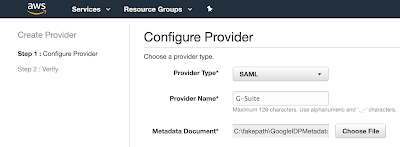
Download the IdP metadata from this screen (we will use it later in the AWS Console).
Set the Name ID Format to “PERSISTENT”
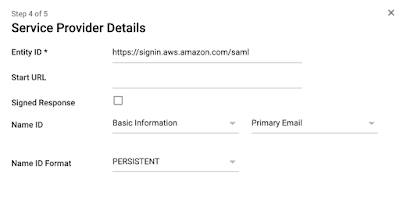
There are two basic attributes that we need to set:
- https://aws.amazon.com/SAML/Attributes/Role – The value of this attribute is a comma separate list of the ARNs of the IAM role and the SAML IdP.
- https://aws.amazon.com/SAML/Attributes/RoleSessionName – The value of this attribute is generally set to the user’s email address.
A limitation of the legacy free version of G-Suite is that you only have a very basic set of user attributes that you can edit and you cannot add additional attributes without “upgrading” from the free version. For my purposes, I will choose an unused attribute “Job Title” to hold the “Role” attribute.
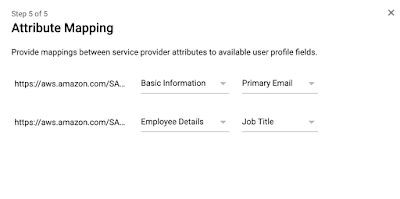
We will go back and enable the application for users and update the “Job Title” attribute after we finish on the AWS side.
AWS Console Steps
From the AWS IAM service we will now create a new SAML provider using the IdP metadata we downloaded earlier.
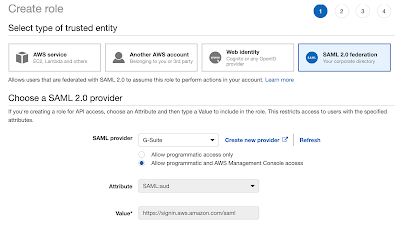
We need a role to assign for the G-Suite Administrator (that’s me).
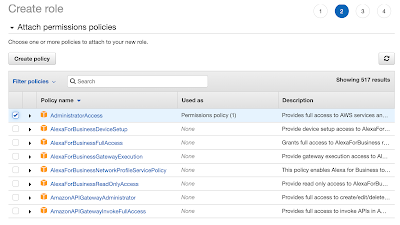
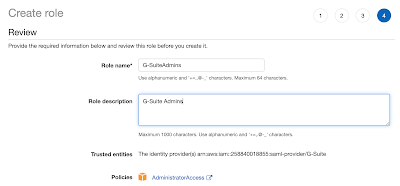
We just need the two ARNs from the Role and the Identity Provider we created.
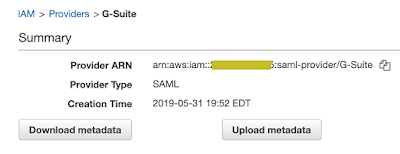
Now back to the G-Suite Admin Console to update the “Job Title” attribute with two ARN values.
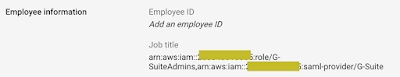
Enable the app for your users and that’s it. Launch the application from your list of G-Suite applications and you should be all set.
Cloud on!